- Connect with Roman Diaz
Threat detection is a fundamental part of a strong cybersecurity strategy that involves monitoring networks, systems and data for any signs of unauthorized access, malicious activities or potential breaches. It plays a critical role in proactive risk management and mitigation, enabling organizations to take timely actions to prevent or minimize the impact of potential threats.
In this article, we examine both traditional and AI-based threat detection. While AI capabilities are incredibly powerful, you’ll see that a multi-layered approach—illustrated by what Microsoft is doing—provides the most comprehensive threat detection.
Traditional Threat Detection Explained
In cybersecurity, threat detection involves actively monitoring an organization’s IT infrastructure and network in real-time to identify and respond to potentially malicious activities or anomalies. The goal of threat detection is to quickly identify indicators of compromise, suspicious behaviors or patterns that could indicate a cyberattack or unauthorized access.
The main objectives of threat detection are:
- Early detection of security incidents to minimize damage and data loss
- Rapid response to contain and mitigate threats
- Continuous monitoring of the network and systems for ongoing protection
Traditional methods of threat detection often rely on rule-based systems, signatures and known patterns of attacks including:
Signature-based detection: Comparing observed data to known patterns (signatures) of known threats
- Pros: Accuracy for known threats, low false positives
- Cons: Inability to detect new threats (zero-day), adaption by attackers, constant updates required (resource intensive)
Behavior/anomaly-based detection: Identifying deviations from normal behavior, which could indicate a potential threat
- Pros: Detection of new threats, adaptability, reduced false negatives
- Cons: High false positives, baseline maintenance hard to establish, resource intensive, behavior variability
Traditional threat detection methods still play a role in cybersecurity, but AI-powered threat detection offers a more dynamic and adaptable approach to identifying both known and unknown threats. Let’s take a look…
AI Threat Detection Explained
AI-powered threat detection is more adaptive and proactive. It uses machine learning algorithms to analyze vast amounts of data, identifying patterns and anomalies that might go unnoticed by traditional threat detection. It continuously learns from new data and adapts to evolving threats to stay ahead of cyber adversaries.
One significant advantage of AI-based threat detection is its ability to process data in real-time. Security products can rapidly analyze massive volumes of information from various sources, including network logs, user behavior and threat intelligence feeds. As a result, potential threats can be spotted and mitigated before they escalate into full-blown attacks.
AI threat detection adds the power of artificial intelligence to the traditional methods of threat detection (anomaly detection, behavioral analysis) and add additional capabilities:
- Machine learning algorithms
- Threat intelligence integration
- Real-time monitoring
- Pattern recognition
- Automated response
- Adaptation to evolving threats
- User and entity behavior analytics (UEBA)
- Deep learning and neural networks
- Data integration
This list will only grow as AI capabilities advance.
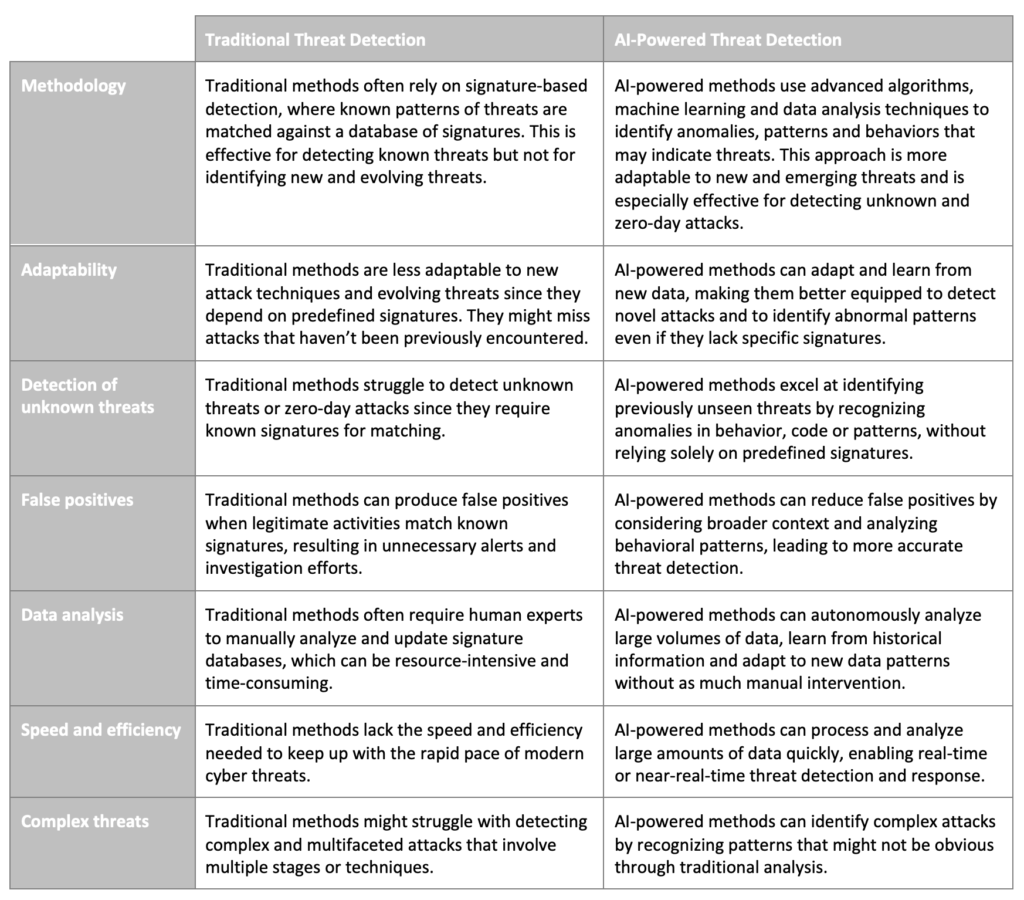
Here’s a comparison of both methods:
Microsoft’s Threat Detection
Microsoft’s approach to using AI-powered threat detection uses advanced analytics and machine learning techniques to detect suspicious activities and potential threats. They’re focused on the integration of extended detection and response (XDR) and security information and event management (SIEM).
XDR aims to enhance threat detection, incident response and overall security by unifying and correlating data from various sources across an organization’s digital environment. XDR goes beyond traditional endpoint detection and response (EDR) solutions by providing a more holistic view of security threats across endpoints, networks, cloud environments and more. It leverages advanced technologies (like AI) to identify and respond to threats in real time.
SIEM is a comprehensive approach to cybersecurity management that combines Security Information Management (SIM) and Security Event Management (SEM) into a single solution. SIEM systems provide organizations with the ability to collect, correlate, analyze and respond to security-related data from various sources across their IT infrastructure.

To simplify which does what:
- SIEM is for event and log aggregation, correlation and monitoring.
- XDR is broader and more proactive. It leverages advanced analytics, automation and cross-platform visibility to identify and respond to a wider range of threats.
- XDR builds upon the foundation of SIEM but offers more advanced capabilities for modern cybersecurity challenges.
Integrating the two is the key to Microsoft’s approach, allowing SecOps teams to perform centralized, context-based threat detection, analysis and response. Read more on this from Microsoft here.
Microsoft’s vision for SIEM and XDR is to deliver an integrated offering that connects Microsoft Sentinel with Microsoft 365 Defender and Defender for Cloud. The technology also supports multi-cloud and multi-platform environments to ensure third-party data and signals are part of Microsoft SIEM and XDR.
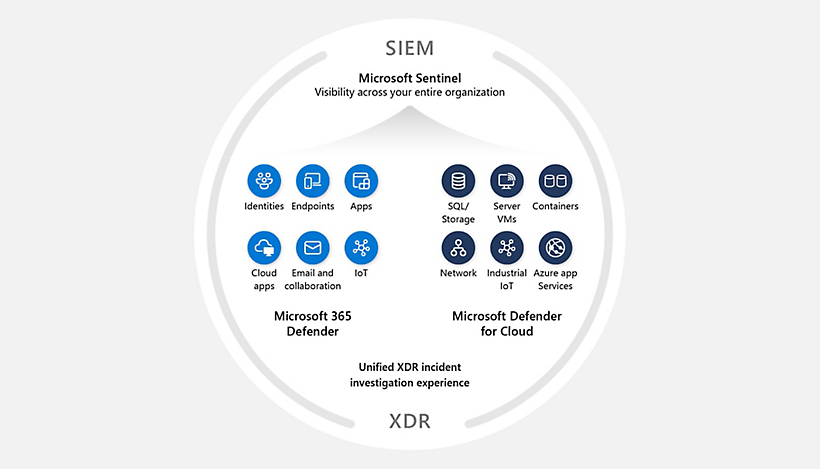
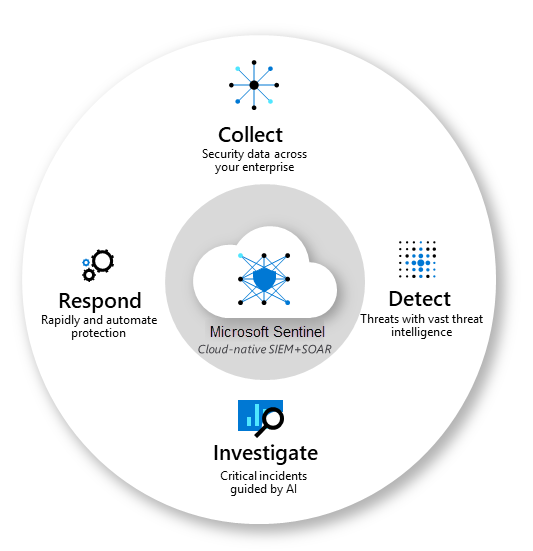
Microsoft Sentinel
Microsoft Sentinel is designed to help organizations collect, analyze, and respond to security events and threats in real-time. It provides intelligent security analytics and threat intelligence, allowing security teams to detect and respond to incidents more effectively.
Microsoft 365 Defender
Microsoft 365 Defender is a unified pre- and post-breach enterprise defense suite that natively coordinates detection, prevention, investigation and response across endpoints, identities, email and applications to provide integrated protection against sophisticated attacks.
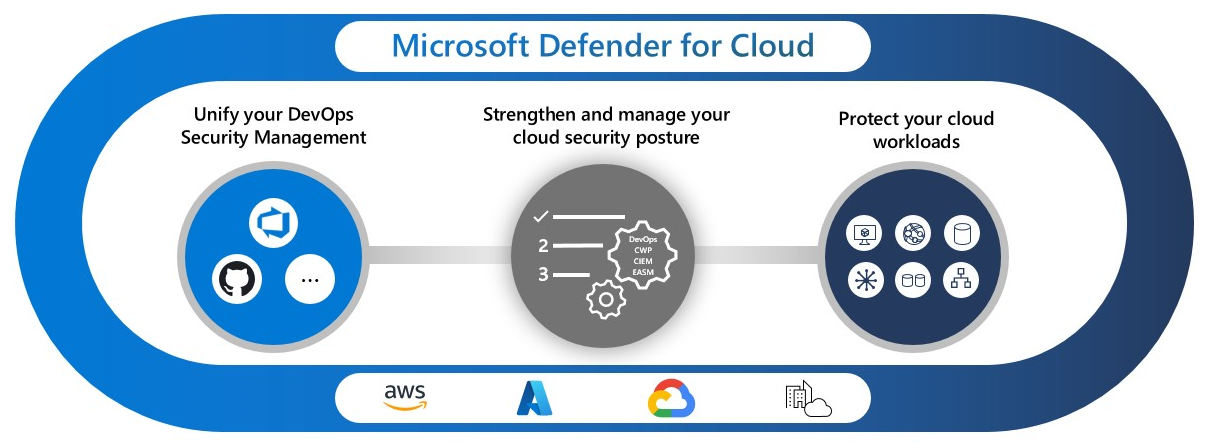
Microsoft Defender for Cloud
Microsoft Defender for Cloud (formerly known as Azure Defender) helps organizations monitor and protect their cloud applications and services. It leverages threat detection capabilities to identify and respond to potential security risks.
Threadfin’s SecOps
In a rapidly evolving digital landscape, the importance of robust threat detection cannot be overstated. As we’ve explored throughout this article, the methods and technologies employed for threat detection have significantly evolved from traditional approaches to more advanced solutions like AI-powered detection, SIEM and XDR. Threat detection is a fundamental part of a strong cybersecurity strategy.
At Threadfin, we understand that protecting your organization is paramount. With the ever-increasing sophistication of cyber threats, relying solely on conventional methods is no longer sufficient. Our team of seasoned IT professionals is well-equipped to guide you through the intricacies of modern threat detection strategies. Whether you’re looking to start from scratch, assess what you have or adopt a completely new solution, we’re here to help.
As you navigate the complex landscape of cybersecurity, remember that staying ahead of cybercriminals requires vigilance, innovation and expertise. Don’t wait for an incident to occur; take proactive steps today to safeguard your digital assets. Your digital future starts with smart choices today. Contact us to learn more.

