Secure | SecOps

Threadfin’s cybersecurity and SecOps services address security risks and cloud security threats proactively and rapidly.
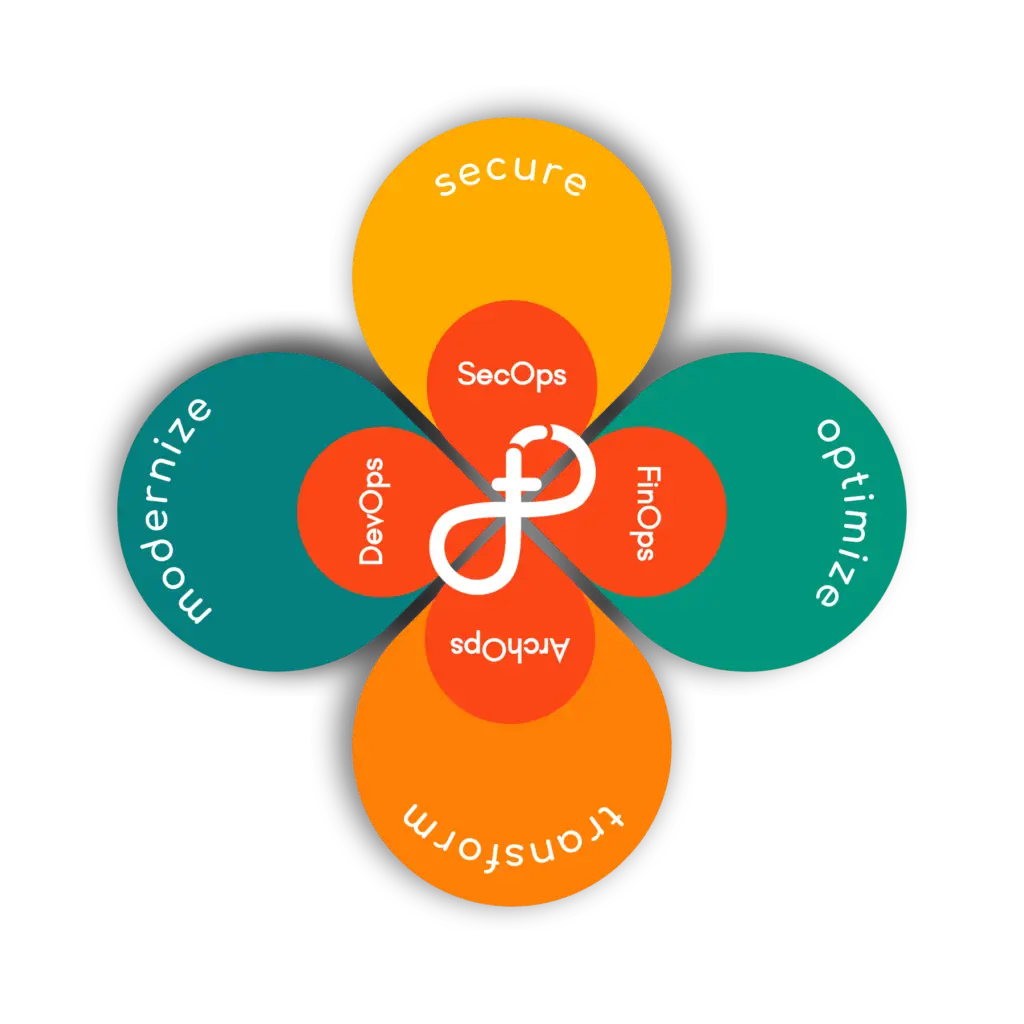
Threadfin uses the Experience Threading Framework to provide solutions that are:

Preventative
Proactive risk management is essential. The need for robust security measures that can evolve as criminals do—and even get ahead of them—has never been more pressing.
Threadfin approaches cloud security threats by addressing security risks at the earliest stage of planning and development—and every stage thereafter.

Responsive
When it comes to dealing with cyber threats, a responsive strategy is critical. This includes real-time monitoring, rapid incident response and continuous assessment of your security posture. Our team integrates proactive measures with operational protocols, ensuring that your security can adapt quickly to any emerging threat.

Rapid
In the event of a ransomware attack or any other severe security breach, quick and efficient recovery is paramount. Threadfin's recovery strategies include comprehensive backup solutions, disaster recovery planning and incident response services designed to restore your operations with minimal downtime and data loss.

Seamless
With a holistic approach to optimized security, our security operations services integrate tools, processes and technology to secure your organization—all while ensuring a seamless user experience.
With Threadfin, your organization gets top-notch security that’s preventive, responsive, rapid and seamless, giving you comprehensive protection against cyber threats.
Threadfin provides human-centered security solutions for safer ways of getting work done.
Depending on your organization’s size and structure, cybersecurity and SecOps can be applied across your entire business or implemented on a project-by-project basis.


Cybersecurity Defined
Cybersecurity sets the overall direction and provides the tools.
Cybersecurity protects digital assets, data and systems through strategy, policies, practices, technologies and frameworks.
Focus: preventive measures
SecOps Defined
SecOps implements and operationalizes security within the strategy, policies, practices, technologies and frameworks defined by cybersecurity.
Security operations services enables real-time monitoring, incident response and ongoing security management.
Focus: Proactive measures & operational integration

Ready to get started?
Threadfin approaches cloud security by addressing security risks at the earliest stage of planning and development—and every stage thereafter.
Here’s what you can expect from our human-centered, experience-driven, outcome-focused security solutions:
Cybersecurity consulting
- Comprehensive security assessments
- Detailed analysis of current security posture
- Identification & mitigation of vulnerabilities
- Ransomware prevention & mitigation strategies
- Email filtering & safe browsing practices
- Regular software updates & patch management
- Security awareness training
- Zero-trust architecture
- Identity & access management
- Network segmentation & micro-segmentation
- Secure access solutions for users & devices
Customized Security Strategies
- Vendor-independent approach for optimal technology integration
- Tailored solutions to address your specific business needs
- Multi-layered approach that leverages AI-powered solutions
- Security policy enforcement
Collaboration & Knowledge Sharing
- Software & cloud security embedded into the development lifecycle for cross-team collaboration
- Partnering with your team for seamless security integration
- Ongoing training & support to empower your staff
Endpoint Security
- Antivirus & anti-malware protection
- Endpoint detection & response (EDR)
- Secure mobile device management (MDM)
- Device encryption & data loss prevention (DLP)
East-west Traffic
- Micro-segmentation services
- Internal traffic monitoring & threat containment
Network Security
- Firewall & perimeter security
- Secure VPN solutions
- Intrusion detection & prevention systems (IDPS)
- Gather & analyze threat intelligence
North-south Traffic
- Perimeter firewall implementation
- Web application firewalls (WAF)
Business continuity & disaster recovery (BC/DR)
- Disaster recovery planning & implementation
- Data backup & recovery solutions
- Business continuity strategies & testing
Ransomware attacks are on the rise. No organization is immune to the threat.
The costs—above & beyond the cost of the ransom (if paid)—can be staggering. But they don’t have to be.

Crafted by our top cybersecurity professionals, our no-cost, comprehensive PRE-Ransomware Checklist includes all the things your IT team should be doing today—proactively—before a ransomware attack occurs.
It’s packed with immediate, short and long-term strategies for backups, architecture and minimized operational impact.
Equip your team to lessen impact and accelerate recovery after a ransomware event.
- Covers key areas: backup systems, data security & business continuity
- Actionable steps for immediate & future planning
- Detailed 5-page resource with 57 critical checkpoints
“You’re thinking about this in a completely different way—thank you!”
—Threadfin Partner
How We Work
Teamwork
Security threats continue to evolve as perpetrators become more creative. Our multidisciplinary outlook raises awareness and inspires more imaginative solutions. Threadfin’s SecOps proactively leverages the expertise of the IT organization to work as a collaborative team.
Trust
We leverage cross-functional teams to keep security and product deployment top of mind with an organization’s ultimate goal: to deliver trustworthy products and services as efficiently as possible.
Reaction speed
Cybersecurity is a constant race against evolving threats and vulnerabilities. It requires continuous learning, adaptation and collaboration to stay one step ahead of cybercriminals.
We use integrated communication, detection and resolution systems that speed up the decision-making process by identifying—and quickly remediating—vulnerabilities.
Consistency
We encourage security and operations teams to work in a non-siloed environment so the pool of resources becomes streamlined. The use of common tools to assess vulnerabilities ensures consistent practices throughout the environment, improving overall efficiency and reducing the possibility of security breaches.