Intelligent Identity & Access Management (IAM) plays a pivotal role in protecting your organization, ensuring that the right individuals have appropriate access to specific resources, systems and data while preventing unauthorized access and potential security breaches.
While some organizations continue to rely on traditional IAM systems with static rules and policies for identity verification and access authorization, more modern adaptive and context-aware approaches are available—and required—to respond promptly to potential threats.
Once you’ve got your domain controller modernized and backed-up (read more here) you want to make sure you have the right IAM solution.
The adoption of modern IAM solutions, such as multi-factor authentication (MFA), single sign-on (SSO) and cloud-based IAM services, had been growing rapidly due to the increased security they offer and their ability to better support remote workforces and cloud-based applications, but not all organizations have made the change. The transition from traditional IAM to modern IAM can take time and resources.
In this article, I examine both traditional and intelligent IAM and make a case for making the move. I also take a look at what Microsoft is doing in this space.
Traditional Identity & Access Management Explained
Traditional IAM refers to the foundational set of practices, policies and technologies that organizations have historically used to manage user identities and control their access to various systems, applications and data. It focuses on establishing and enforcing access permissions, ensuring security and adhering to compliance requirements.
Key characteristics include:
- User provisioning and deprovisioning: Traditional IAM systems handle the creation, modification and deletion of user accounts and access privileges. This process is often manual and requires administrative intervention.
- Authentication: Traditional IAM typically uses username and password combinations for user authentication. While some organizations may implement two-factor authentication (2FA), it is not as prevalent as in modern IAM systems.
- Authorization: Access control in traditional IAM relies heavily on role-based access control (RBAC), where users are assigned roles with predefined access permissions. These roles are static and may not adapt to changing user needs or contexts.
- Access requests: Users typically submit access requests to IT administrators who review and grant access based on predefined policies and procedures. This can be a time-consuming process, leading to delays in granting access.
- Single Sign-On (SSO): SSO solutions are often part of traditional IAM, allowing users to access multiple applications and services with a single set of credentials. However, these SSO solutions may not offer the same level of flexibility and integration seen in modern IAM.
- Manual auditing and reporting: Auditing and compliance reporting are typically manual processes in traditional IAM. IT administrators are responsible for generating access logs, monitoring user activity and ensuring compliance with regulatory requirements.
- Limited context awareness: Traditional IAM systems may not take into account contextual factors like user location, device or behavior when making access decisions. Access permissions are primarily based on predefined rules and roles.
- High administrative overhead: Managing user accounts and access permissions can be labor-intensive, requiring significant administrative effort and resources.
- Limited self-service: Self-service capabilities for users, such as password resets or access requests, may be limited in traditional IAM systems, leading to increased reliance on IT support.
- Scalability challenges: Traditional IAM systems may struggle to scale efficiently as organizations grow, especially in large and complex environments.
Traditional IAM can’t fully address the evolving security threats, user demands and regulatory requirements of today’s digital landscape. Intelligent IAM solutions, on the other hand, incorporate advanced technologies like artificial intelligence (AI) and machine learning (ML) to provide more adaptive, context-aware, user-friendly IAM. Let’s take a look…
Intelligent Identity & Access Management Explained
Intelligent IAM is an advanced approach to managing and controlling access to digital resources and systems within an organization. It combines traditional IAM principles with AI and ML techniques to enhance security, user experience and operational efficiency. Key components and features include:
- Identity management: This core component of IAM involves the creation, maintenance and management of digital identities for users, devices and applications. Intelligent IAM systems use AI and ML to automate identity provisioning, de-provisioning and lifecycle management while ensuring security and compliance.
- Access control: Intelligent IAM employs adaptive access control mechanisms. It assesses various factors, including user behavior, location, device type and context to determine access permissions dynamically. This allows for more fine-grained and context-aware access decisions, reducing the risk of unauthorized access.
- Authentication: AI-driven IAM solutions often incorporate advanced authentication methods, such as biometrics (e.g., fingerprint or facial recognition), behavioral analytics and multi-factor authentication (MFA). These methods enhance security by making it harder for unauthorized users to gain access.
- Authorization: Intelligent IAM systems use machine learning to develop and refine access policies over time. They can adapt to changing user roles, behaviors and business requirements, ensuring that users have the right level of access without unnecessary restrictions.
- Behavior analytics: Machine learning algorithms analyze user behavior patterns to detect anomalies and potential security threats. If a user’s behavior deviates from their usual patterns, the system can trigger alerts or impose additional security measures, such as step-up authentication.
- Privileged access management (PAM): PAM is a critical component of Intelligent IAM, focusing on controlling and monitoring access for privileged users and accounts. It ensures that administrators and other high-privilege users have the necessary access without compromising security.
- Adaptive risk-based policies: Intelligent IAM systems assess risk factors in real-time and adjust access policies accordingly. For example, if a user attempts to access sensitive data from an unfamiliar location or device, the system may require additional verification steps.
- Self-service and user experience: Intelligent IAM aims to provide a seamless and user-friendly experience. Users can often reset passwords, update profiles or request access themselves, reducing the burden on IT support.
- Compliance and auditing: These systems assist in meeting regulatory compliance requirements by maintaining comprehensive audit logs, generating reports and ensuring that access controls align with compliance standards.
- Integration and scalability: Intelligent IAM solutions can integrate with various other security tools and systems, such as Security Information and Event Management (SIEM) systems, to provide a holistic security posture. They are also designed to scale with an organization’s growth.
Here’s a comparison of both methods:
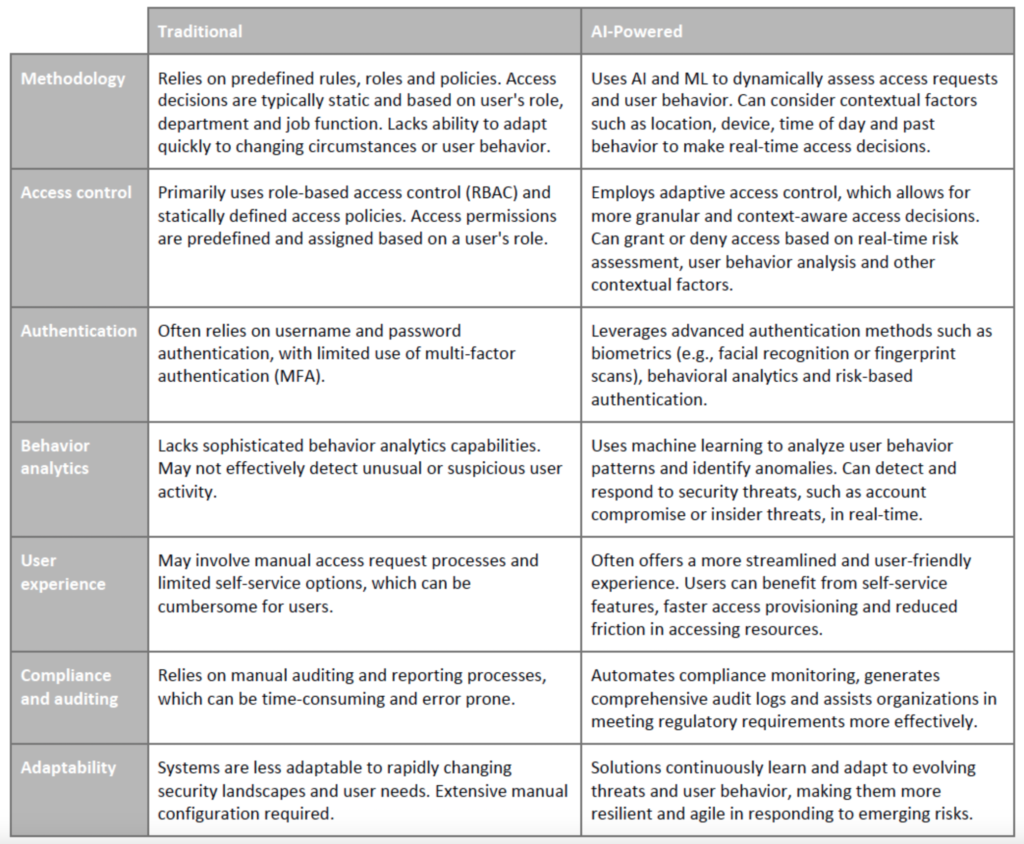
AI-driven IAM represents a more advanced and adaptive approach. It addresses the limitations of traditional IAM by providing dynamic, context-aware access control and improved threat detection capabilities.
Microsoft’s IAM | Current Events
Last month, Microsoft began enabling a stronger form of multifactor authentication in Microsoft Entra ID to improve security for tenants that have the registration campaign feature set to the Microsoft managed state.
On September 15, 2023, they began a 6-week campaign that prompts users who authenticate using SMS and voice methods to set up the Microsoft Authenticator app when they sign in to their work or school account within the next 3 logins.
Authenticator is the preferred method of MFA so this is a smart move. If you can’t set up authenticator or you’re having trouble setting up FIDO2 and Oauth, let me know (ro********@*******in.com). Threadfin can definitely help.
Microsoft’s IAM | General Thoughts
Identity management providers vary, but I’m a big fan of Microsoft’s Entra (formerly Azure Active Directory). Whether you’re coming from a cloud-based option like Okta or an on-premises solution, Microsoft has made huge advancements—something not everyone has recognized quite yet.
Here’s where I think it really stands out:
- AI-enhanced identity verification: Advanced biometric authentication, like facial recognition and fingerprint scanning, bolster the traditional username and password approach. By incorporating AI into these processes, Microsoft’s systems can analyze user behavior patterns, location information and other contextual data to verify identities more accurately, reducing the risk of unauthorized access.
- Adaptive access control: Microsoft’s adaptive access control leverages AI to evaluate risk factors and dynamically adjust access permissions based on real-time conditions. For instance, if a user attempts to access corporate data from an unusual location or device, the AI system may enforce additional authentication steps or restrict access until the user’s identity is verified.
- Threat detection and anomaly monitoring: The system continuously analyzes user activity and access patterns, flagging suspicious activities that may indicate compromised accounts or insider threats. Security teams can take swift action to prevent unauthorized access or data breaches.
- Privileged Access Management (PAM): Focused on controlling access to highly sensitive resources, PAM systems use AI algorithms to automatically assess privilege requests, evaluate risk factors and grant access based on predefined policies. This approach minimizes the risk of misuse or abuse of privileged accounts.
- Passwordless authentication: Through the adoption of biometric authentication methods and security keys, users can securely access their accounts without the need for passwords.
Specific products include:
- Microsoft Entra ID (formerly Azure Active Directory)
- Microsoft Entra ID Governance allows for entitlement management, lifecycle workflows, AI-driven and standard access reviews and privileged identity management for users or groups.
- Microsoft Entra External ID will allow organizations to manage external identities—those of customers and partners.
If you’re still using traditional IAM or you want to make sure your intelligent IAM is exactly what you need, Threadfin can help. Contact us today.

